Imagine spending millions on high-tech locks for your house only to leave your front door wide open. That’s what a security misconfiguration is—a glaringly avoidable gap in your cybersecurity defenses that gives hackers a free pass to your digital assets.
A single misconfiguration can undo years of cybersecurity investment”—and the statistics back this up. Over 95% of cybersecurity breaches are due to human error.
As Rob Gluckin, CEO, GTG Networks famously put it: “Hackers aren’t smarter than your security team; they’re just more persistent in finding your overlooked mistakes.”
Let’s dive into what is a security misconfiguration and why it’s often the Achilles’ heel of even the most sophisticated organizations.
Still Exposed to Misconfigurations?
Don’t let a preventable mistake turn into your next data breach.
Understanding Security Misconfigurations
Think of a security misconfiguration as a digital oversight—a setting or a lack of settings that unintentionally exposes your system to risk. These mistakes may seem small, but their impact can be catastrophic.
How Misconfigurations Happen
- Default Settings: Many IT teams forget to change factory defaults on devices or software, leaving doors wide open.
- Excessive Permissions: Granting unrestricted access to users or applications increases the risk.
- Unsecured APIs: Poorly configured APIs become treasure troves for cybercriminals.
- Ignored Patches: Outdated software is a magnet for hackers who exploit known vulnerabilities.
Real-Life Security Misconfiguration Examples
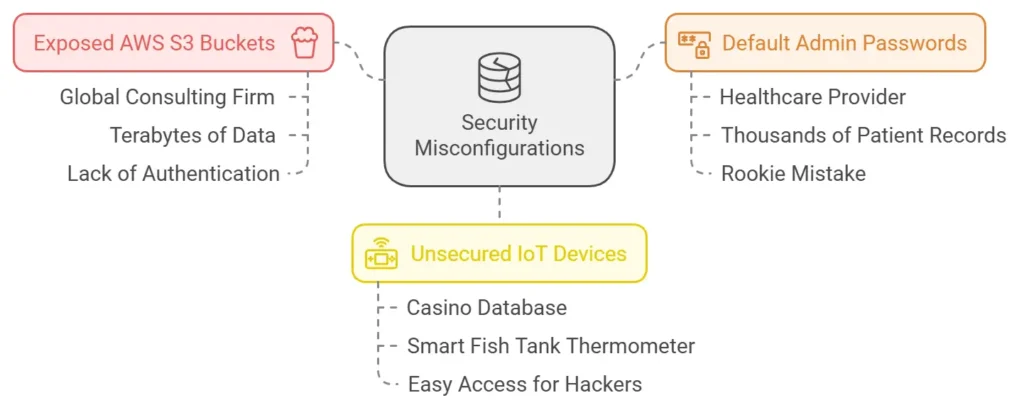
1. Exposed AWS S3 Buckets
In 2017, a global consulting firm exposed terabytes of sensitive data, including passwords and client information, due to an open AWS S3 storage bucket. A simple lack of authentication turned a routine error into a PR nightmare.
2. Default Admin Passwords
A healthcare provider’s database was breached because its admin interface was left with the default password. This rookie mistake compromised thousands of patient records.
3. Unsecured IoT Devices
Hackers infiltrated a casino’s database via a smart fish tank thermometer. Yes, a thermometer! It was connected to the network without proper security protocols, providing easy access to the hackers.
These security misconfiguration examples highlight the risks: even minor lapses can snowball into massive breaches.
The Anatomy of Security Misconfiguration Attacks
How do attackers exploit security misconfigurations? They follow a methodical process:
- Reconnaissance: Using automated tools, they scan for vulnerable systems—like a thief checking for unlocked windows.
- Exploitation: Once they find a weak point, they gain unauthorized access, inject malware, or steal data.
- Impact: Depending on the breach, this could mean financial theft, data corruption, or reputational damage.
One of the most infamous security misconfiguration attacks occurred in 2019 when a cloud storage misstep exposed the personal data of 540 million Facebook users. Hackers didn’t need to break through firewalls; they simply walked through an open door.
Why Security Misconfigurations Are So Dangerous
Misconfigurations are the cybersecurity equivalent of forgetting to lock your car. They’re easy to overlook but incredibly inviting to criminals. Here’s why:
1. They’re Invisible Until Exploited
Unlike a malware attack, misconfigurations don’t trigger alarms. You might not know there’s an issue until it’s too late.
2. They Scale with Complexity
The more tools, software, and cloud services your business uses, the higher the chances of misconfigurations slipping through the cracks.
3. They Can Be Automated
Hackers use bots to scan for vulnerabilities in bulk, meaning they don’t need to target you specifically—they just need to find an error.
How to Fix a Security Misconfiguration Vulnerability
Preventing misconfigurations isn’t rocket science, but it does require discipline and the right tools.
Step 1: Audit Everything
Start by auditing your entire IT environment. Tools like Qualys or Nessus can automate this process, scanning for misconfigurations across servers, networks, and applications.
Step 2: Harden Your Systems
System hardening means minimizing vulnerabilities by:
- Disabling unused features.
- Changing default passwords.
- Applying the latest security patches.
Step 3: Limit Permissions
Adopt a “least privilege” approach. Every user or application should have access only to what they absolutely need—nothing more.
Step 4: Automate Configuration Management
Using tools like Ansible or Puppet, you can enforce secure configurations automatically. This reduces human error and ensures consistency.
Step 5: Monitor Continuously
A one-time fix isn’t enough. Continuous monitoring ensures that new vulnerabilities are caught before they can be exploited.
Key Tools and Strategies for Preventing Security Misconfigurations
| Tool/Strategy | Purpose | Benefit |
|---|---|---|
| Configuration Management Tools (e.g., Ansible, Chef, Puppet) | Automates consistent system configurations across environments | Reduces human error and ensures security settings are enforced |
| Cloud Security Posture Management (CSPM) | Monitors cloud environments for misconfigurations | Detects public exposure risks and compliance violations |
| Role-Based Access Control (RBAC) | Restricts access based on user roles | Prevents excessive permissions and unauthorized access |
| Regular Penetration Testing | Simulates attacks to uncover vulnerabilities | Identifies misconfigurations before attackers can exploit them |
| Security Information and Event Management (SIEM) | Aggregates and analyzes logs for abnormal activities | Enables real-time detection of potential misconfigurations |
| Training for IT Teams | Educates teams on best practices for configuration | Reduces likelihood of errors due to lack of knowledge |
Conclusion: Take Action Before It’s Too Late
A security misconfiguration vulnerability may seem trivial, but it can act as a gateway to catastrophic breaches. By auditing your systems, enforcing strict permissions, and automating configurations, you can close these gaps before attackers find them.
Your business deserves more than basic protection. GTG Networks specializes in identifying and addressing vulnerabilities like misconfigurations, ensuring your systems are secure and resilient. Contact us today for a consultation and take the first step toward bulletproof cybersecurity.


